Welcome to my latest article where we're going to explore the fascinating world of data security. I know, I know, I've written about cybersecurity before, but this time, we're going to focus specifically on data security.
Data security is all about keeping your digital information safe from hackers and other unauthorized individuals. With more and more data being stored online every day, it's becoming increasingly important to understand the best practices for keeping that information secure. Whether you're a business owner, an employee or just someone who uses the internet, knowing how to protect your data is crucial in today's digital age. In this article, we'll break down some technical concepts and strategies that you can use to safeguard your data, without needing a degree in computer science. So, let's dive in!
What is Data Security?
Do you love having your personal information kept safe and secure? Well, that's what data security is all about! It's the process of protecting digital information from unauthorized access, use, or theft. This can include anything from data stored on your computer or phone to information transmitted over the internet.
Data security is incredibly important for both businesses and individuals, as it helps prevent identity theft, data breaches, and cyber-attacks. If your data gets hacked, it can cause all kinds of problems, like losing money, ruining your reputation, and even getting into legal trouble. So it's crucial to know how to protect your data and keep it safe from those who would misuse it.
Common Threats to Data Security
Let's take a closer look at some of the most common threats to data security:
Phishing: You know that pesky email from your "bank" or "online retailer" that asks you to click on a link to update your information? That's a classic example of a phishing attack. Cybercriminals use this tactic to trick you into giving away your sensitive information like your passwords, credit card numbers, or social security information. Remember, always be cautious of emails from unknown sources, and never click on suspicious links or download attachments from unknown senders.
Example of a phishing email:
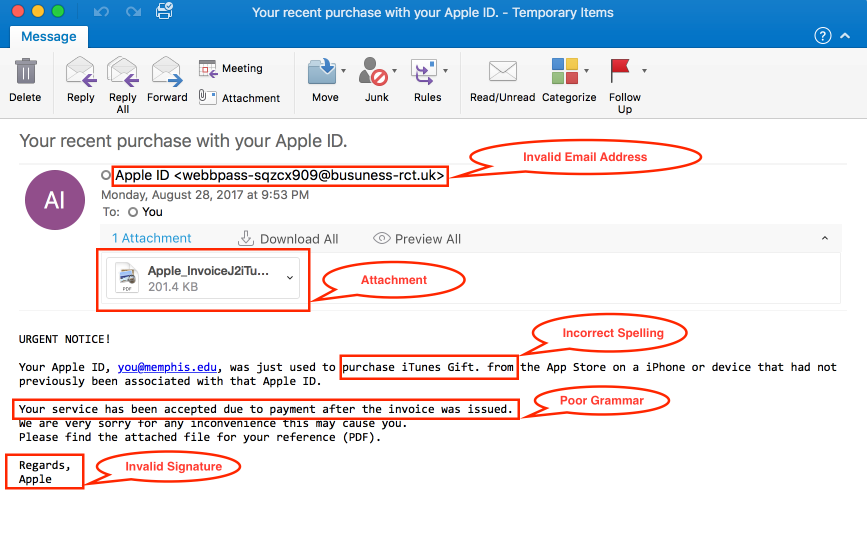
If you receive an email requesting personal information, it's essential to be cautious and verify the legitimacy of the request. Here are some steps you can take:
Check the sender's email address: Scammers often use fake email addresses that mimic a legitimate organization. Check the sender's email address to ensure that it's from a reputable source.
Look for spelling and grammar errors: Many phishing emails contain spelling and grammar errors. Legitimate organizations usually have professional communication, so be cautious of poorly written emails.
Don't click on any links: Phishing emails often contain links that lead to fake login pages or infected websites. Never click on links in suspicious emails.
Call the organization: If you're unsure about the legitimacy of the request, call the organization's customer service number and ask if they sent the email.
Report the email: If you determine that the email is a phishing attempt, report it to the organization being impersonated, as well as your email provider.
Remember, it's always better to be cautious than to risk your personal information falling into the wrong hands.
Malware: Malware is any type of software designed to harm your computer system, steal your data, or even take control of your device. This can include viruses, spyware, or ransomware, which encrypts your files and demands payment to restore access. Malware can be spread through email attachments, file downloads, or even visiting an infected website. So, be sure to keep your antivirus and firewall software up to date, and only download files from trusted sources.
Password attacks: Have you ever used "123456" as your password? You're not alone, but unfortunately, it's also one of the easiest passwords to guess. Cybercriminals use password attacks to gain access to your accounts by guessing your password or using software to crack it. It's essential to use strong and unique passwords that include a mix of numbers, letters, and symbols. Also, consider using two-factor authentication for an extra layer of security.
Insider threats: Insider threats can come from employees, contractors, or anyone with authorized access to sensitive information. These can be intentional, such as employees stealing data for personal gain, or accidental, such as an employee inadvertently sharing sensitive information. To mitigate this risk, companies should have strict access controls, monitor employee activity, and provide regular training on data security best practices.
Overall, it's crucial to stay vigilant and take proactive measures to protect your data. By understanding these common threats and implementing best practices, you can help keep your digital information safe and secure.
Best Practices for Data Security
To protect your digital assets, you must implement the following best practices:
Keep software up-to-date: Make sure to regularly update your operating system, software, and applications to fix security vulnerabilities. For example, if you're using a Windows computer, make sure to enable automatic updates so that you're always protected against the latest threats.
Use strong passwords: Using strong passwords that are hard to guess is essential for keeping your accounts secure. A strong password should be at least 8 characters long and include a mix of uppercase and lowercase letters, numbers, and symbols.
Enable two-factor authentication: Two-factor authentication adds an extra layer of security by requiring a second form of identification, such as a fingerprint or code sent to your phone. This can help protect your accounts even if your password is compromised. For example, many banks now require two-factor authentication to access your account.
Encrypt sensitive data: Encryption is the process of converting data into a code to prevent unauthorized access. Encrypt all sensitive data, both when it's stored and when it's transmitted. For example, if you're sending an email with sensitive information, you can use an email encryption service like ProtonMail.
Use a virtual private network (VPN): A VPN provides a secure connection between your computer and the internet. It encrypts your online traffic and hides your IP address. This can help protect your online activity from prying eyes. For example, if you're working remotely, you can use a VPN to securely access your company's network.
Be cautious with email: Do not open email attachments or click on links from unknown sources. Be especially wary of emails that ask for sensitive information. For example, if you receive an email from a bank asking you to update your account information, it could be a phishing scam.
Backup data regularly: Regularly back up your data to an external hard drive or cloud storage. This ensures that you can restore your data in the event of a data breach or other disaster. For example, you could use cloud backup services like Google Drive or Dropbox or OneDrive to automatically back up your files.
In today's digital age, data security is critical to keeping your digital assets safe from cyber threats. By following some simple best practices, you can significantly reduce the risk of data breaches and cyber-attacks. Remember to regularly update your software, use strong passwords, and encrypt your sensitive data. Also, be careful with emails and regularly back up your data to ensure you can recover it in the event of a disaster. Keep these tips in mind to protect your digital assets and keep your online presence secure!
References
- Example of a phishing email: University of Memphis


